Wireguard
RouterOS7 added alot of new features to Mikrotik routers. One of my favorite is Wireguard implementation. Wireguard is modern VPN solution, which can replace good know OpenVPN. Everyone who configured OpenVPN or IPSec know how difficult it could be. Wireguard is much easier, it shouldn’t be a problem even to home user. In this tutoral we will configure Road Warrior VPN. Mikrotik hAP AC3 as Wireguard VPN Server and Windows 10 as client.
Mikrotik
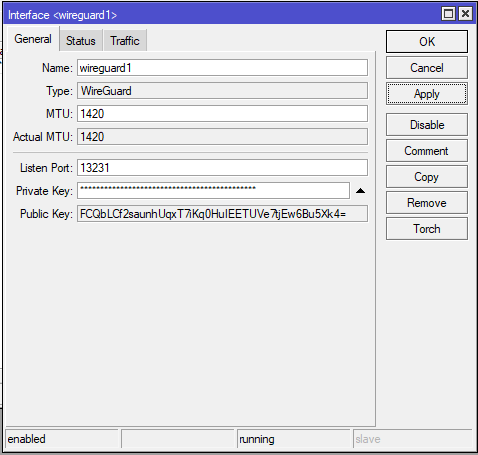
Remember to upgrade Winbox to the latest version. From right side menu click on Wireguard then ADD:
- Name: type anything
- MTU: leave 1420, but if you have connections problem, change it to 1412
- Listen Port: Wireguard port, leave default
- Public Key: generate automatically when applied
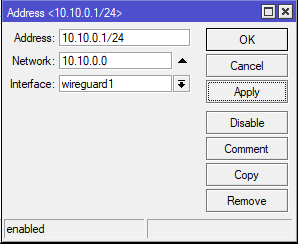
In the next step we add IP Address to our new interface. Choose IP->Addresses and add new topic. No matter what subnet you choose, i prefer 10.10.0.0, so my ip interface is 10.10.0.1/24, don’t forget to add /24 at end and set Interface to wireguard1
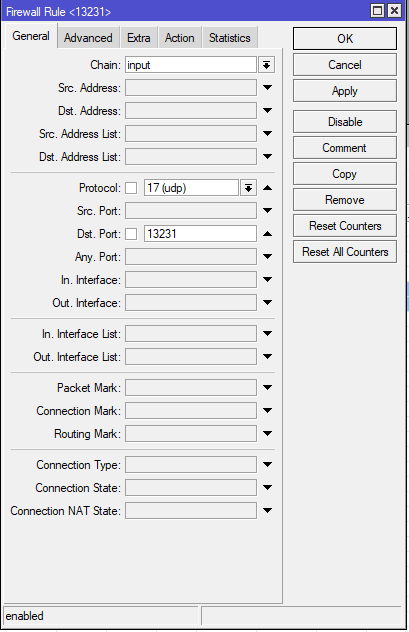
One of the last things on Mikrotik is open Listen Port. We use default 13231 UDP port. Switch to IP->Firewall and add new rule.
- Chain: input
- Protocol: udp
- Dst. Port: 13231
- Action: accept
Windows 10 Config
Go to Wireguard official site and download the latest client version. Installation proces is ver easy, just few click on Next. After successfully install, you should see Wireguard icon on system tray. Right click on it and add empty tunel.
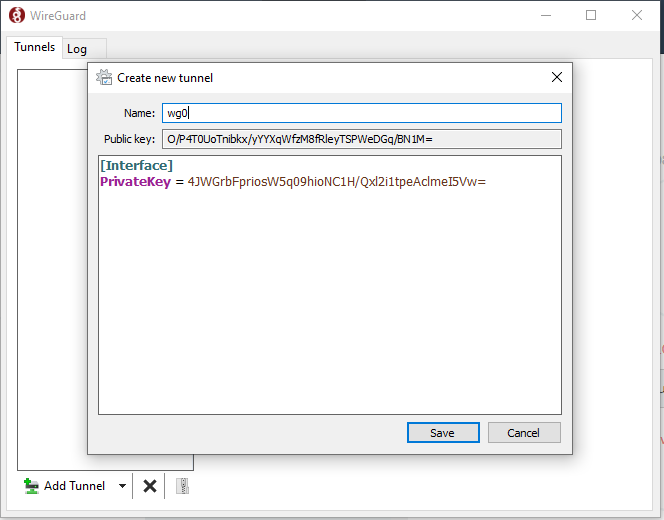
Wireguard tunnel configuration is text-based, we can setup all settings in one window. According official documnation Name field should contains wg0, wg1, wg2, as interface name. Of course we can use any vaule, but better keep one standard. The pair of keys will generate automaticlly. Copy Public Key and switch back to Mikrotik->Wireguard and click on Peer.
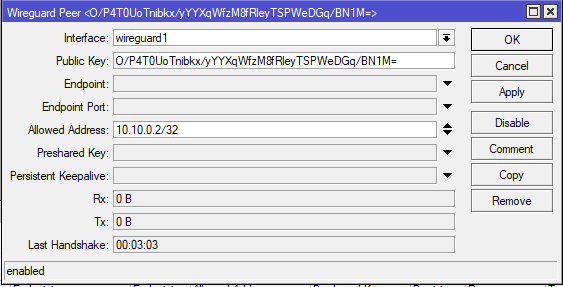
Interface set to wireguard1, paste public key from windows 10 client machine. Our Mikrotik Router works as VPN Server, so leave Endpoint and Enpoint Port blank(we will used it in Site-to-Site VPN). Earlier we set 10.10.0.1/24 as IP Address to wireguard interfeace, Allowed Address means what client’s IP is, choose IP from same subnet with /32 mask.
Switch back to Windows 10 and Wireguard tunnel configuration.
Wireguard Tunnel configuration
[Interface]
PrivateKey = 4JWGrbFpriosW5q09hioNC1H/Qxl2i1tpeAclmeI5Vw=
Address = 10.10.0.2/32
DNS = 8.8.8.8
[Peer]
PublicKey = MjlNUhE0u2X+ecX5rJOcrsTsr2xwbM9VYTsiJHXsfB4=
AllowedIPs = 0.0.0.0/0
Endpoint = 46.77.89.232:13231
PersistentKeepalive = 10
- Address: same as Mikrotik Peers configuration
- DNS: public or Mikroitk IP Address
- Public Key: WireGuard public key
- Allowed IPs = if you want tunneling all traffic throught Mikrotik set 0.0.0.0/0
- Endpoint: Public IP and Port Mikrotik router
- PersistentKeepalive: if you’re behind NAT or a firewall and you want to receive incoming connections long after network traffic has gone silent, this option will keep the “connection” open in the eyes of NAT.



hey bro, good article! How to connect printer throught wireguard tunnel between 2 mikrotiks with 2 offices?
hi, you have to add static routing between networks behind routers. Add it on IP->Routes.
WireGuard is such a clean, well-implemented, versatile VPN protocol. I was so happy when RouterOS v7 was finally supported on my Mikrotik hEX router and I could run WireGuard natively!
Hi, can Mikrotik act as a wireguard client to another Mikrotik which is a wireguard server – Dial Up VPN (Mikrotik is a client and server)? Client (Mikrotik) is behind NAT and doen’t have a public IP address.
Yes, Mikrotik can be used as a VPN client.
could you please show how would you configure mikrotik as a roadwarrior ?
Please add the Wireguard setting in the newer version of Router OS 7.14+
There have been some changes, it would be worth taking them into consideration.